Over the last seven years, our role as Chief Information Security Officer (CISO) has gained significant importance within communities, because communities that want to be in line with the Baseline Information Security Government urgently need such a CISO. About 50% of the job vacancies on LinkedIn are directed towards communities. But the role of CISO drastically changed in recent years. The latest figures indicate that an astonishing 22% of the IT budget is allocated to cyber and information security. Our own experience is that dialogues with C-level execs nowadays revolve around questions such as: Are we doing the right stuff, and are we doing this stuff right? How do we measure and monitor our return on security investments (ROSI)? And where do we get the ‘biggest bang for the buck’?
In this article, written by our own prof. dr. Yuri Bobbert, academic director of the Business & IT Master’s at Antwerp Management School, we will first elaborate on three main perspectives that define the organizational scope of the CISO. These different levels require different viewpoints and focus areas in the dialogue about the ROSI. Secondly, we will look at the future capabilities of the CISO.

Three main perspectives to define the organizational scope
1. Conversations at board level
At board level, the CISO must provide an overview of and insight into the largest cyber risks. That insight must reflect relevant sources of information security and risk information within and outside the municipality. Ideally, its impact on the organization and stakeholders is expressed in economic terms. But it is just as much about Corporate Social Responsibility (CSR) and Sustainable Development Goals (SDGs). This means that the CISO is also responsible for the accuracy and reliability of the required source data. Organizations that do not take sufficient care of their data, digitization, risks, and security will fall by the wayside.
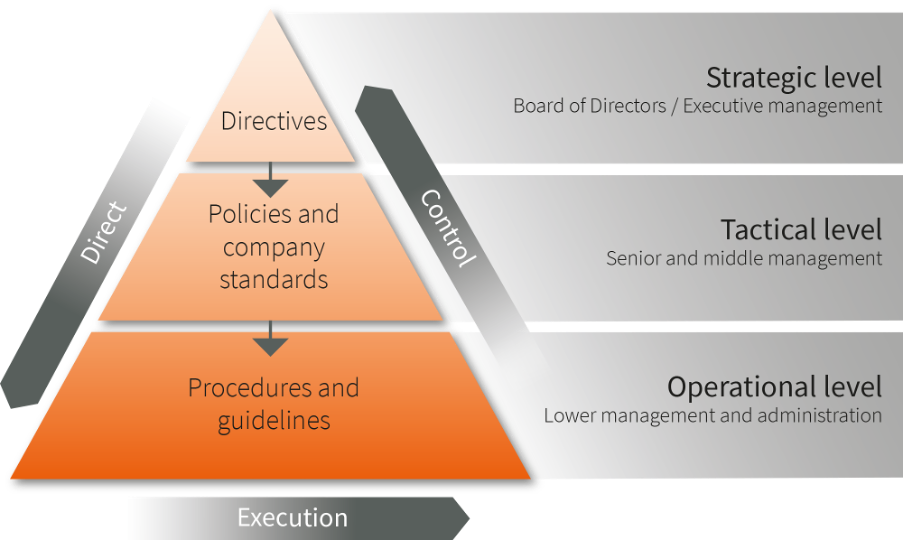
2. Conversations at managerial level
At the second level, insight into and overview of the correct responsibilities is relevant. The primary responsibility of managers at this level is to ensure that the company's DNA is infused with adequate security, risk awareness, responsibility, leadership and craftsmanship. The most important role for the CISO here is as that of a doctor who constantly provides diagnoses to determine who needs appropriate treatment, while helping to make the right decisions. Think of system or data owners of the Municipal Civil Administration who take "ownership" over their systems and therefore also think about a sufficient degree of security level and sufficient budget space for this. Nowadays you can no longer just leave this to the IT department. The IT department is purely facilitating, ownership and accountability do not lie with IT.
3. Conversations at operational level
The implementation of cybersecurity is done at the operational level. The biggest challenge for all reasonable-sized organizations with a high degree of IT is dynamically aligning technical implementations with their internal or external cyber threat requirements. Smart cities must consider GDPR requirements when collecting citizen data, which often prescribe technical measures. Research by Antwerp Management School has shown that a large majority of organizations do not meet these technical requirements.
After two full years of implementing the European regulation, information security and its measures appear to be the most challenging issue for companies to comply with. A quantitative analysis of the most violated GDPR articles, conducted by law firm CMS, shows that the type of GDPR violation with the highest sum of (publicly published) fines imposed since GDPR enforcement is the "insufficient technical and organizational measures to ensure information security". As stated in Article 32 of the GDPR, companies must ensure the security of information, in accordance with their capabilities, resources and technologies available on the market. This doesn't necessarily give companies much more insight into what to do, and how to do it to "secure" their data.
This legislation also assumes that those responsible have sufficient knowledge and skills to do this.
Effective IT security collaboration, orchestration and administration are thus required to reduce the stress and inaccuracy faced by CISOs in this area.
Future capabilities of the new Cyberleader
The role of the CISO is gradually expanding to ‘economist’, ‘talent magnet’ and ‘orchestrator’ with a clear vision on how to address the pitfalls at the three organizational levels.
Economist because the CISO must be able to rely on detailed, reliable source data to determine cyber risk in the context of all other risks and be able to clearly outline the benefits of the costs incurred. The CISO must be able to explain and sell to the board of directors where the highest value is obtained from investments in security, based on facts and figures.
Talent magnet due to the ongoing talent war for security specialists. Research shows that the digital security profession has seen substantial growth in its global ranks, rising to 3.5 million people currently working in the field, adding 700,000 professionals in absolute numbers, 25% more than last year’s estimated workforce. This represents a decrease in the global workforce shortage, now down to 3.12 million from the 4.07 million deficit reported last year. Data suggests that employment in the field now needs to grow by about 41% in the US and 89% globally to close the talent gap. This is a problem, especially as vocational qualification or internships are not a hard entry requirement in this profession; contrary to, for example, lawyers, civil-law notaries, and doctors.
Orchestrator because “third-party risks” are the greatest risk to platform-based business models that operate in a broad eco-api-based system and need clear, predefined indicators to monitor their performance across multiple environments. This means that the CISO must orchestrate the security of the entire chain to get a complete view of the effectiveness of the security measures. Think of DIGI-D connections, UWV, SVB, Tax Authorities and other types of chain integrations where data exchange takes place. In my latest book, I list 10 successful strategies to make government platforms more secure.
By carrying out these three roles effectively, you can have relevant conversations with all stakeholders, regardless of the organizational level at which you interact or the topics you discuss. CISOs who can contribute to the dialogue on where to get the most value from security investments will win the hearts of their directors and supervisors.
Do you also want to further educate yourself in digital transformation to strengthen your organization? Discover our part-time executive master’s & masterclasses here.



