Over the last years, the role of Chief Information Security Officer (CISO) drastically changed. Over the last decade, I have seen this industry explode with fuzzy vendors in the cyber domain all delivering point solutions. Is this because industry strategy agencies like IDC , Gartner, and Forrester predict that security spending keeps on increasing? Or is it because the cyber consumer just follows the herd? The latest figures indicate that an astonishing 20% of the IT budget is allocated to cyber and information security . IDC states; “However, you can spend 15% of your IT budget on security and still not achieve the level of assuredness that you desire if your architecture is sufficiently complex or the assets being protected are especially valuable. Likewise, a spend of 5% may be appropriate.”
My experience is that dialogues with C-level execs nowadays are about: are we doing the right stuff, and are we doing this stuff right? How do we measure and monitor our return on security investments (ROSI)? And, where do we get the best return on our security investments to master the Wicked problem of Cyberrisk[1]. A dialogue, that very few suppliers actively participate in, while interacting with their CISO customers.
To get more context on the "CISO attention" issue, let's first elaborate on three main perspectives that define the organizational scope of the CISO. These different levels require different viewpoints and attention points in the dialogue about the return on security investments.
The overarching problem for nowadays CISOs is to separate the sense from the non-sense. Non-sense being the complete wood of FUD sellers, sense being in- and oversight into the relevant issues particular to the three organizational levels.
Dialogues at the board level
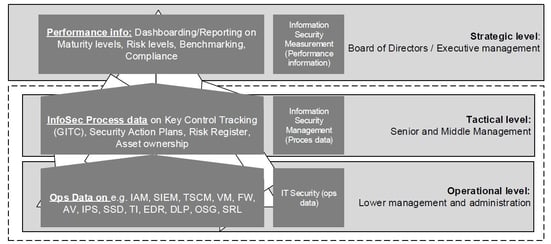
On the board level, the CISO must deliver insight and oversight into major cyber risks. This insight must be reflected from relevant infosec and risk intelligence sources inside and outside the company. Its impact on the company and its stakeholders must ideally be expressed in economic terms.
But these days, the board's responsibility goes beyond strict financial performance Organizations must demonstrate good governance and take sincere ownership of Corporate Social Responsibility (CSR)[1] and associated Sustainable Development Goals (SDGs). They need to take ownership of the "wellbeing of the firm". Therefore, the CISO is also responsible to assure the accuracy and reliability of the source data which provides insight into these not strictly financial goals. From this perspective, it should be no surprise that that half of all C-level executives have cybersecurity issues on their board's agenda once a quarter. Companies lacking adequate care for their data, digitization, risk, and security are in the end losing the game.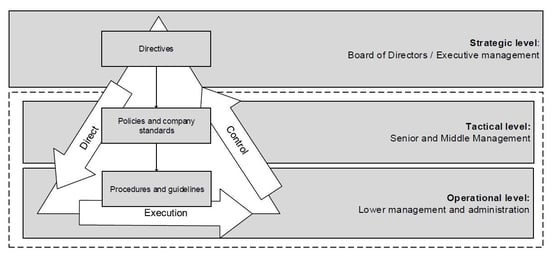
Dialogues at the managerial level
On the second (managerial) level insight and oversight on proper risk and security ownership is relevant. The main responsibility of managers at this level is making sure that the company's DNA is vaccinated[1] with a sufficient amount of security, risk awareness, ownership, leadership, and craftsmanship. The main role of the CISO is that of the doctor who constantly diagnoses who needs proper treatment and helps to make the right decisions, rather than being perceived as the "red tape general".
On this managerial level business and asset owners must rely on clearly predefined Key Risk and Performance Indicators (KRI/KPI) that are standardized through the company and orchestrated into the technology, people and processes[2]. This sounds like an open door, but these processes require a serious effort to implement in large and complex environments. They often lack the capabilities and architectural talent to translate this risk strategy into the operations. I've first hand observed many companies struggling with operational security processes and technology such as micro-segmentation, security operations, and incident response.
Dialogues at the operational level
The foundation of cybersecurity is established (e.g. designed and engineered) in the operational level of the organization. They are responsible for getting relevant and reliable infosec and risk intelligence information from sources inside and outside the company
The operational level is the nerve system of the organization. The main problem for all organizations, with a reasonable size and technical legacy, is to dynamically align technical implementations with their internal or external requirements with cyber threats that manifest themselves quick and in an unpredictable manner. In chapter 3 of my book I describe in detail the major struggle CISO’s have to align these three levels of Governance to Management to Operations and how collaboration, orchestration and administration reduces the stress and inaccuracy[1] CISO’s have to deal with.
Despite enormous progress in the industry, inaccuracy remains an enormous challenge for many organizations. The proof is provided by inadequate detection rates and response times[2] to attacks. But the stakes are high. An inadequate and seemingly weak response to breaches can lead to a negative impact on the perceived value of the firm and potentially the share price. This stresses the necessity for further end-to-end architecting and orchestrating security policies into cloud based technology such as End Points, Pipelines, Containers and further automation of the controls and their proof of effectiveness to demonstrate proper assurance to the top. This craftmanship is to my opinion the main reason why 50% of the C-level execs including CISO’s want to outsource their SOC[3] and gain more “bang for their buck”.
Three roles for the modern CISO
I see the role of the CISO expanding to “economist”, “talent magnet” and “orchestrator” with a clear vision to address the pitfalls at the three organizational levels.
- Economist since the CISO needs to rely on detailed reliable source data to determine the cyber risk level in the context of all other risks. And explicating and selling to the board the "biggest bang for the buck", based on facts and figures. This is why we educate in our ISM module “Cybereconomics” and risk quantification techniques.
- Talent magnet because of the ongoing "war" on security talent that anchors risk and security leadership, craftsmanship and ownership to continuous "sharpening the saw"[1] and streamline the operation. To in the end demonstrate reasonable assurance over the Information and Cybersecurity function from bottom to the top. This means the CISO needs to lead and influence the hiring process of top-notch staff that is capable of vaccinating and positively influence risk and security owners. Talent that is capable of engineering KRIs and KPI mechanisms into the technology and processes.
- Orchestrator because "third-party risks" are the biggest risk for platform-based business models working in a large eco-api-based-system that require clear predefined indicators to monitor the cyber performance over multiple environments (from left to right). This means that the CISO needs to architect and orchestrate the security of the entire chain. So he or she gains full visibility on the effectiveness of the security controls.
In conclusion, we can state that CISOs that are equipped with hard and softskills to start and lead the dialogue on strategic, tactical and operational level are ending up winning the end game.



