“How on earth does cybersecurity relate to the subject of sustainability?” was what some students at the Antwerp Management School must have thought when the AMS guest lecture of Ad Krikke started. Sustainability still triggers most people's thoughts about environmental challenges threatening our planet. Yet, if you take a broader Environment, Social and Governmental (ESG) view of how organizations perform on various sustainability and ethical issues in a Digital world, it becomes clear how Cybersecurity, or rather Digital ethics, could play a role. I (Professor Yuri Bobbert) invited Ad Krikke from the global research company Gartner for this lecture at Antwerp Management School, and together we did collective research via an exciting dialogue with the students, support by a Group Support System.
When we asked the students; “can we sustain a digital world where we have to worry about the continuity of our critical infrastructure?”, “can we sustain a world where you have to worry about the privacy of your data?”, and “can we sustain a digital world where we worry about algorithms (in social media) and AI that could impact our personal safety and our mental health?”, it made perfect sense that Cybersecurity is all about sustainability. It also explains the development of various European regulations for digital (GDPR, NIS2, DORA, AI act) that focus precisely on these ESG topics. This is yet another topic that will not be solved automatically. Yet I’m optimistic that most entrepreneurs feel a responsibility to act sustainably when creating new Digital business opportunities for themselves. I even believe we should stop looking at Cybersecurity as solving a problem and instead look at it as creating opportunities AND taking responsibility.
 In Krikkes lecture, he presented several use cases that have found these “win-win” solutions. Yet it calls for more diversity and a closer collaboration between various skill-sets to build digital solutions. Most engineers are very focused on building the most powerful technical solutions, this must be augmented with other skill-sets that can help to address ESG challenges and find business opportunities as well. The good thing is that digital solutions nowadays are built by technical engineers and business representatives, with a focus on creating great(er) user experiences. Gartner research shows that most organizations are moving to new I&T operating models, democratizing IT, and owning digital sustainability topics is felt by up to 76% of these business representatives. Other research shows that many organizations already include cybersecurity & privacy in their ESG reporting (in 2021, 334 of S&P 500 organizations reported on Cybersecurity in ESG report).
In Krikkes lecture, he presented several use cases that have found these “win-win” solutions. Yet it calls for more diversity and a closer collaboration between various skill-sets to build digital solutions. Most engineers are very focused on building the most powerful technical solutions, this must be augmented with other skill-sets that can help to address ESG challenges and find business opportunities as well. The good thing is that digital solutions nowadays are built by technical engineers and business representatives, with a focus on creating great(er) user experiences. Gartner research shows that most organizations are moving to new I&T operating models, democratizing IT, and owning digital sustainability topics is felt by up to 76% of these business representatives. Other research shows that many organizations already include cybersecurity & privacy in their ESG reporting (in 2021, 334 of S&P 500 organizations reported on Cybersecurity in ESG report).
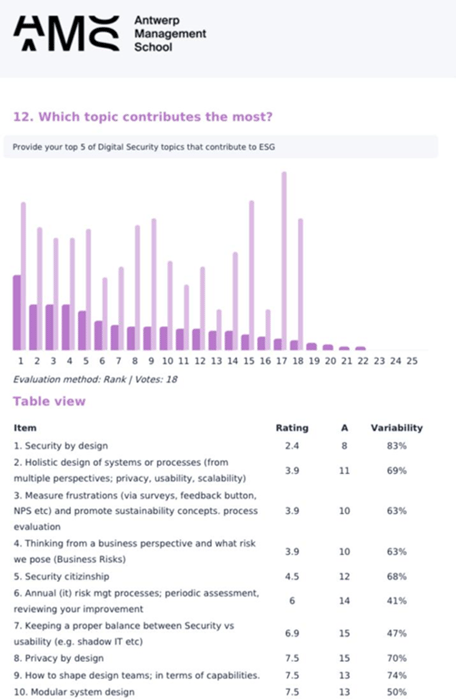
Together with the students, we examined which security initiatives could contribute to create more sustainable IT solutions. The concept of Security by design came up. This means that you take risk, security and compliance requirements in consideration in an earlier stage of the business development. Security by Design ended up with a relatively high score yet with a large variability, meaning there is a substantial variance in opinions. This group variance started the conversation on “inside-out thinking” to be combined with “outside-in thinking”. The inside-out way of thinking is focused on risk avoidance and putting processes and policies in place to achieve security goals. Security by design fits very well in this way of thinking. Adding outside-in thinking, focus on how the various stakeholders perceive the risk and the controls, needed. If stakeholders perceive a negative customer journey of putting controls in place or too much friction from the security controls itself, it will limit the effectiveness of these controls. Yet if we provide a great user experience which includes low friction AND a safer feeling when using the tool, that takes care of our security and privacy, this will be perceived as a relief. And much more engaging for all stakeholders. This is in line with some of the group research findings of “the holistic design (#2) view”, running “friction” surveys (#3) and put yourself in the position of the (business) stakeholder (#4). These are all mentioned by the students as contributors to sustainability.
Another interesting remark was: Aggressive deleting of data (to avoid Data obesity)
so you don’t have to protect and don't have to maintain it (storing, deleting, encrypting etc). (Storage/compute power consumes much (fossil)power). This is completely in line with the desire for governments to collect and store less data. [1]
Outside In & Security by Design
An example of outside in thinking is the Lockchain project within NN Group. This project was initiated by a bunch of cross thinkers (omdenkers) that looked at the traditional security and risk management process the company called upon itself and inherited over time but never scrutinized on purpose and effect. The Lockchain team developed new, easy, and effortless workflow technology to guide an average manager through setting digital security requirements and assigning these to owners with clear instructions. This technology was successfully adopted throughout the entire organization because it was perceived as a tremendous relief (compared to the previous way of working) and way more effective for DevOps Teams due to the precision of applying controls proportionally. The full story is published here and resulted in the commercialization of the technology.
Conclusion:
Developing an outside-in approach to digital security helps to look at things from multiple perspectives and consider multiple stakeholders' interests. For example, to appraise Artificial Intelligence technology and take society, ethical, sexual [2], legal and author rights into account, so you don’t harm others and ad-hoc ban technology [3]. But scrutinize the potential risks from the view of multiple actors to make an informed decision which lasts longer, is trustworthy and adheres to regulations (such as AI Act). E.g. a sustainable decision.
This also helps us to move away from the endless debate about implementing controls towards exploring new markets and try out new things. Becoming the department of “yes”. Since they recognize opportunities and understand customer journeys and dilemmas, like in the Lockchain case, they think as entrepreneurs and can think in simplicity rather than complexity. Ultimately, this will lead to a self-fulfilling prophecy of teams and people wanting to work with the security by design department that is “built to last [4]”.
|
[1] |
https://open.overheid.nl/documenten/ronl-246810f1-5ab0-4556-9774-280cbd1cf5e0/pdf |
|
[2] |
R. Goodman, "Why Amazon’s Automated Hiring Tool Discriminated Against Women," aclu, 12 10 2018. [Online]. Available: https://www.aclu.org/news/womens-rights/why-amazons-automated-hiring-tool-discriminated-against. [Accessed 17 4 2023]. |
| [3] | [3] A. Scroxton, "Italy’s ChatGPT ban: Sober precaution or chilling overreaction?," Computerweekly, 5 4 2023. [Online]. Available: https://www.computerweekly.com/news/365534355/Italys-ChatGPT-ban-Sober-precaution-or-chilling-overreaction. [Accessed 17 4 2023]. |
|
[4] |
Jim Collins wrote the bestseller: Built To Last Successful Habits of Visionary Companies. The book provides a master blueprint for building organizations that will prosper long into the 21st century and beyond. |
Prof. Dr. Yuri Bobbert is Academic Director at AMS.


